We are living in a very unusual time, in fact, personally, 2020 is the most challenging year thus far, and I see the reflections of it in my business and personal life. But times are filled with transformational opportunities rather than allowing us to sharpen the same old knife again and again.
At Aventude Spark-E, we are working with some interesting social distancing induced business cases, and one aspect exciting to me is building architecture & social distancing. It was a request from one customer to obtain technical advisory on how to augment the existing evacuation planning simulations to map social distancing. If you haven’t heard about evacuation planning simulations, simple googling will help, it is a well-established agent-based simulation to study and aid evacuation planning at an event of a catastrophe.
We started it with matching eye-contact based simulation (I was surprised when I saw it first), and it seemed to work well. However, the critical issue is, these simulations are expensive and often loaded as part of pricy software. Also, this software need specialized hardware and processing. Those reasons didn’t map well when we did cost curve analysis for a SaaS application.
Either we have to reduce the cost of the implementation or augment the problem statement to attract the investors and expand the audience. Second option seemed more feasible than first, but how to make it to the mass audience. An idea came across the table, why don’t we make it a standard and we will put social distancing index for each building, that every building has to do it and qualify this index.
An engineering simulation soon became a standardization business – in the back of my head I was thinking, ok, this is how standards are born lol. We gave that task to someone who’s specialized in that area, and started thinking about how to bring more crispy use cases.
At this stage, we were working mostly at the conceptual level or thought leadership level as our PR team prefers that way (wink). Whether the social distancing index would fly or not, the requirement to modify existing buildings and their interiors is a fascinating use case. Most businesses are facing a struggle on how to bring the customer back; it is not enough for them to show they cleaning shoes and tables every hour. Something has to structurally convincing for people to feel safe, because we are fighting against an invisible enemy.
We did some R&D with Revit with a structural engineering designer from customer side, who helped us to do standard simulations and interior basics. The eye contact simulation which already exist, we thought to tap into it and see how things can work together.
The prototype, seemed to be working well.
- Revit Python SDK is used to study the existing CAD drawing of a building structure
- It plays a simulation in encode base to identify the eye-contact rate at a given occupancy rate – there are suggestions to use ray-tracing simulation and lighting as well, but we haven’t tried it yet.
- Revit layer to suggest interior changes to reduce the eye contact rate, which is mapped to the social distancing index.
#3 is challenging but doable; the real challenge is suggesting a building architecture with meaning and taste. Say if you’re a coffee shop, the algorithm should know what are the possible things to put in and re-arrange things in a way that are relevant to your business. It is entirely different from modelling a library. This is the super end goal, but will not be part of the initial release, or it may be available as a preview feature for a particular segment of buildings.
Leaving the details, this is a compelling case in terms of how we are trying to address a creative industry and applying AI to augment it. At this level, a complete AI would be very expensive (or a better way to put it; we still do not know how to make it cost-effective). Now the model suggests the structural elements. These models are more structural that they do not possess aesthetic value; that’s where human creativity and emotion play a role. It is not a real-time human to AI interaction; the baby steps are in more of a guiding mechanism for the designers.
I love to see an AI, that re-models an interior of an existing building, we send a drone or something to capture the building model, and it suggests changes with minimal investment with the current stuff adhering to the preferred choices of interior design.




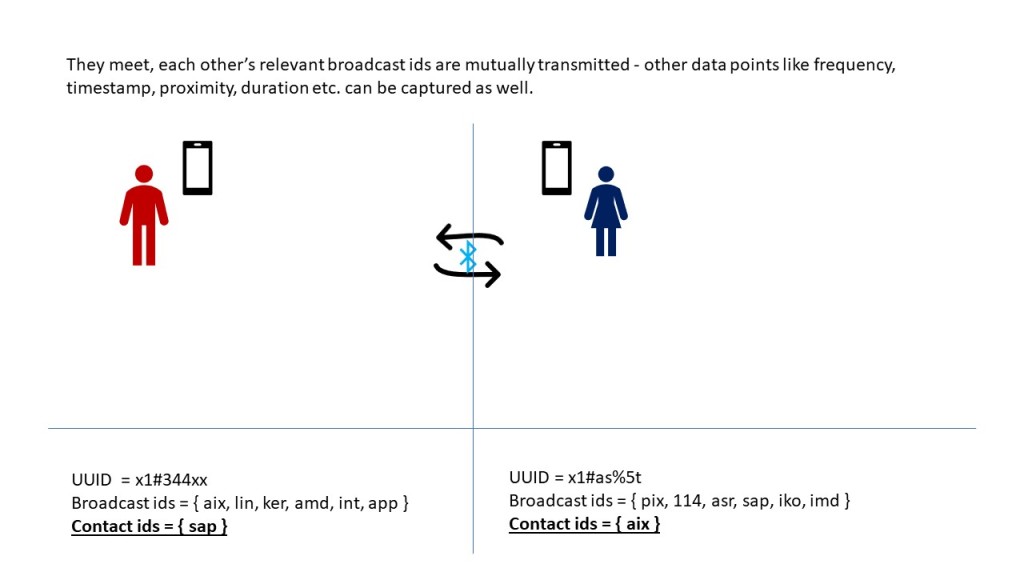
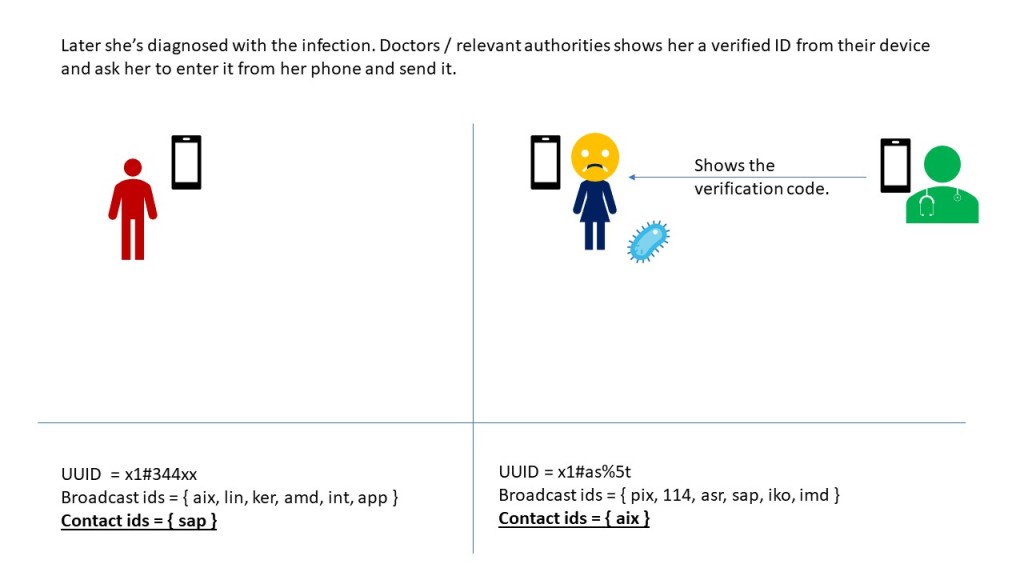
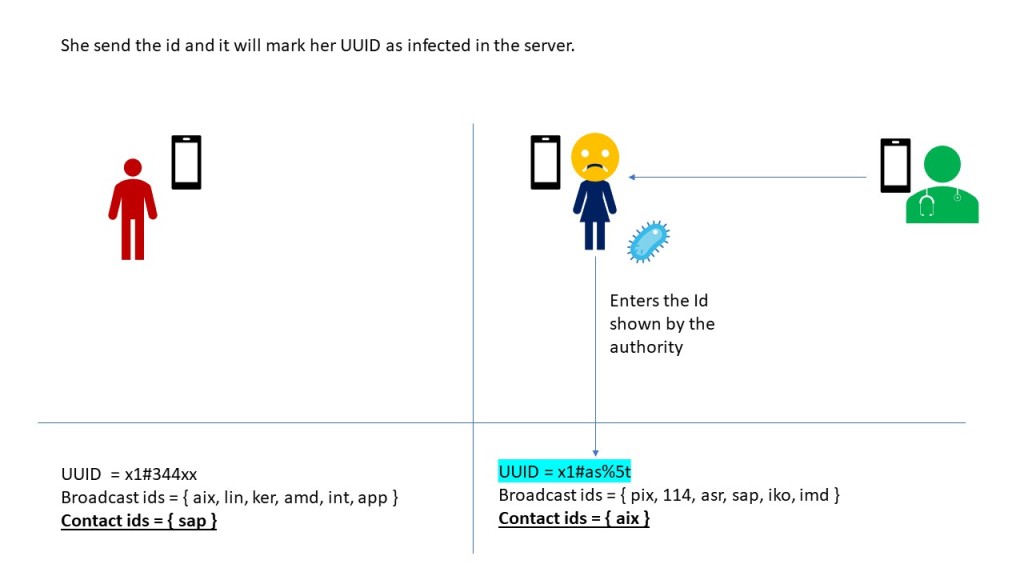
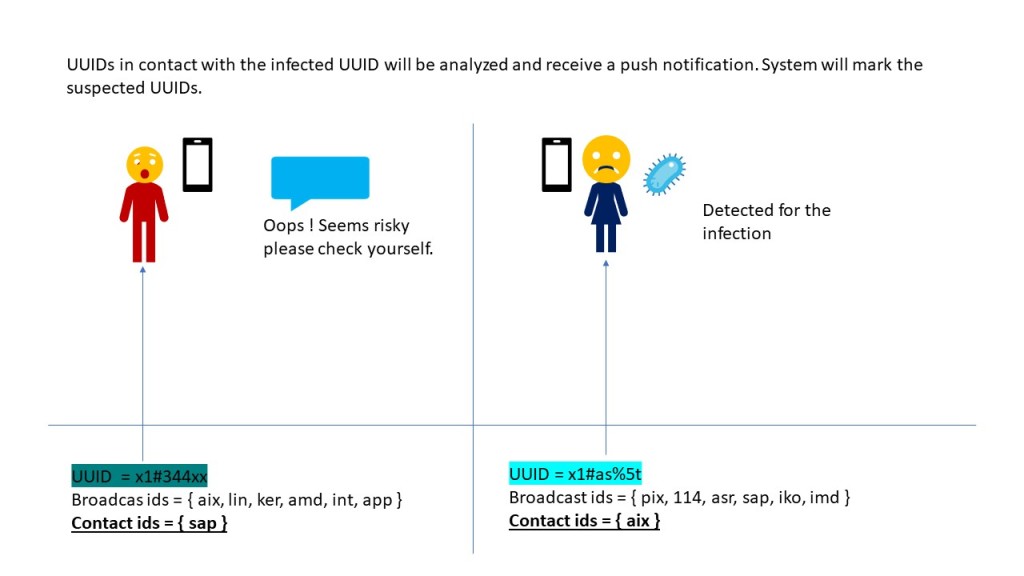
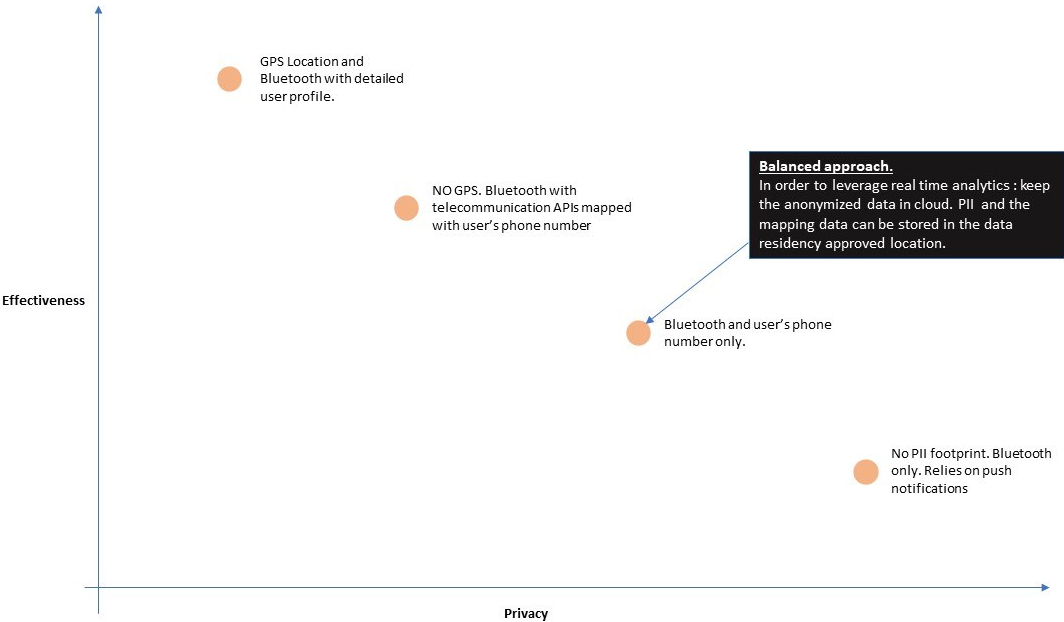


 Source: Frost & Sullivan, 2017
Source: Frost & Sullivan, 2017






